BRAINTREE
Lisa Stebic, John Spira, Stacy Peterson
Chapter 4
The Cell Phone:
Illegal Wiretaps
The most interesting symbol in this 11.29.08 session is on page 3 where they show a “cell phone” that is a “tape recorder”—which means that specific phone is being “tapped and recorded” as mention in Chapter 1 associated with “Lafarge” and the “cassette tape recording”, see 12.01.08 page 2 [link to 12.01.08 session].
The “big white animal’s paw” was holding this cell phone in his hand—he had it in his hand. In a later session, they show the animal paw holding the cassette tape while pointing the finger at me.
He is the one who has been pointing the finger at me all these years.
 That cell phone—shown to me on November 29, 2008—is the same cell phone as in this photo taken January 7, 2014. And this is the cell phone I am using right now!
That cell phone—shown to me on November 29, 2008—is the same cell phone as in this photo taken January 7, 2014. And this is the cell phone I am using right now!
That means nearly seven years later, “7 man Seven” is STILL tapping my phone illegally.
That is also the same cell phone that was shown to me on 03.08.10 page 11 as posted above in the “Lafarge” references in Chapter 1.
Spirit has shown me multiple different cell phones throughout these nearly seven years; and each one they’ve shown to me I end up having without realizing I was shown that phone previously.
 There is no way for me to remember every detail and event contained in the thousands of pages of information I have and as I’ve been shown over a seven year period; precisely why I am adamant about detailed documentation to have as a reference.
There is no way for me to remember every detail and event contained in the thousands of pages of information I have and as I’ve been shown over a seven year period; precisely why I am adamant about detailed documentation to have as a reference.
I did not realize this particular phone I have now was shown to me back in November of 2008 until I was reviewing my notes in this session on July 31, 2013.
This cell phone was first mentioned on 11.17.08 page 2. And the skinny version of what the 11.07.08 session means: this whale—Moby Dick—is going down because of me.
The phone I now have came to me through a sequence of events completely out of my control and this phone was not of my choosing. The individual who gave me this phone has no idea of my work on MISSING and these psychic sessions I have published; therefore they have no idea I made a drawing of this phone more than FIVE years ago. There is no denying that spirit showed me a detailed image—and I drew it and then published that drawing—of the phone I am currently using—five years before I had the phone. That cannot be denied.
There also can be no denying that spirit clearly showed me in that session that everything I do on this phone is being RECORDED. Hence some of the ludicrous messages I have sent to myself the past few months to get this idiot to use the information contained in those messages and trap him more than what I’ve already done to trap him.
He steals my information in his effort to be the next great big famous law enforcement agent using his success in the surface world to be the mask for his underground and underwater world success—the new way of modus operandi for those operating in the underground world.
They never leave the underworld. They merely operate on the surface as the distinguished gentleman, businessman, philanthropist, politician, etc; but in reality, their success is formed in the operation of their criminal underworld. All you need to accomplish that level of deception is to write a book then start appearing on talk and news shows and you’re in at the next level.
That’s the “code”—one of their “Ten Commandments”.
Upon the discovery that my current phone was continuously being recorded, I began to send text messages to myself. I’ll send one about a particular topic and point to my journals as a reference to whatever I choose to base my statements upon. After I send the initial text message to myself with plenty of case details containing truths, part-truths, no-truths, and false-truths, I then send out another message later—to myself so he can steal it from me—and that message contradicts the previous message in part or in whole or whatever pops into my head at the time. I try to have fun with it while still sounding so serious and dramatic. I do this haphazardly yet consistently.
If he has plagiarized that information I’ve sent to myself or if he is using it someway in his pathetic investigation, then he is making a complete fool of himself in the process; and that is precisely what I intended for him to do.
Who is in control here?
No matter how difficult, how large or how insurmountable something may appear to be, almost any obstacle can be overcome when you use your brain, you stick to it and you never give up.
07.06.09 shows a touch screen cell phone—a style of cell phone I was not familiar with at the time and why I described it as “sleek”. This cell phone is associated with when “she gets the boot.” This black and charcoal gray sleek-looking cell phone is a “purple” square someone is trying to force into a round container. That symbolism should speak on its own without the need for me to interpret its meaning. Lisa Stebic is represented by her favorite color—purple—and that is the cell phone. The cell phone is also a pack of “cigarettes” that is a pack of “Paul Mall” along with “IQ”.
The “IQ” refers to a comment I make in Chapter 11 about investigators and their use of computers in investigations as referenced by the symbol from the words of a song: “Don’t talk to strangers.”
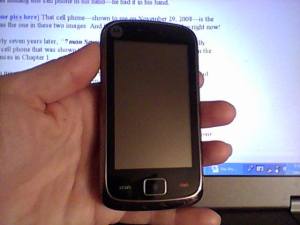 This is the cell phone I used in mid-latter 2011 through early 2012.
This is the cell phone I used in mid-latter 2011 through early 2012.
What that 07.06.09 page 1 tells me is that “she” is going to get fired for what “he” did—he being “Joe” who is the “Pall Mall” heavy smoker guy who is also “Puffing Paul” on Topix.net. He is going to “frame her”—anything to keep the pressure off him by redirecting it onto another, no matter whom that other is. He is so despicable; he would setup his own mother.
“Puffing Paul” is also “aka Russell”—both Topix.net posters and both fictitious identities that were a part of the “orphanannie clan of posters as detailed in Chapter 6.
At this time in 2009, my home phone and my computer activity was illegally being tapped and recorded obsessively. I have proof of that. But what I’d like to point out is what is on page 2. And this is Lisa telling me where her remains are.
 On 07.06.09 page 2 they show me precisely where Lisa Stebic’s remains are. And that is where he is—this is “John”—the one who is in control—“John Jr.” who is “Tony” undercover. I was shown a “valve” and this valve was “underground” and was associated with “hydraulics”. This valve is also associated with “Pistone” as shown to me after this date.
On 07.06.09 page 2 they show me precisely where Lisa Stebic’s remains are. And that is where he is—this is “John”—the one who is in control—“John Jr.” who is “Tony” undercover. I was shown a “valve” and this valve was “underground” and was associated with “hydraulics”. This valve is also associated with “Pistone” as shown to me after this date.
“Pistone” is symbolic to “Joe Pistone”. “Joe Pistone” is symbolic to “Joe Swift” who is also “j” and the “j. Connolly” person, symbolic to the “son” of “John Connolly”—a former Boston FBI agent who was “Whitey Bulger’s Handler” and is in prison for protecting Whitey Bulger. “Joe Swift” is the “rising son” who is the “covert operative”—the “under cover” person whose cover I blow again in Chapter 10—and this man being symbolically represented as “j Connolly” tells me that he is the “son” of the “handler” who was, is, or will end up in prison for protecting the mob boss he was assigned to take down.
The symbolic meanings are always connected and never limited—they mean multiple things at the same time. Remember the plethora of false identities created to distort perception so nobody can understand it; and keep in mind that Tony’s children are his cover.
THE FOLLOWNG IS EXCEEDINGLY IMPORTANT:
 *NOTE:* This is not the real “Tony”. This is a picture of a real person whose images he has cloned and plagiarized in an effort to maintain his charade and his cast of fictitious characters.
*NOTE:* This is not the real “Tony”. This is a picture of a real person whose images he has cloned and plagiarized in an effort to maintain his charade and his cast of fictitious characters.
A week or two after I conducted the 07.06.09 session that showed me the “valve” and before I posted it on MISSING, this guy—Lisa’s killer—emailed this photo to me. Look at the valve behind this guy. My radar was up on this guy from the get-go but now it was on high alert.
In an effort to verify what I already suspected about this guy and his involvement in Lisa Stebic’s disappearance and murder, I established contact with him via email (yet he thought he had one on me); and his internet IP in the summer of 2009 came in as a “wireless” IP from a phone with a “Roselle, Illinois” location.
They used police issued “blackberries” to access the internet from their computers.
Using a blackberry for an internet connection allows the user to grab an IP from an exterior location, so when they post on internet forums such as “Topix.net”, the IP will come up as whatever one they choose it to come up as.
For example, when you utilize a Blackberry as your internet provider to connect your computer to the internet through a USB connected Blackberry phone and the Blackberry software, you get a random IP location generated by the software through the mobile carrier. These IP locations range from anywhere within the United States. Once the computer has an established Blackberry issued IP connection, you then set out to make a random post on Topix.net in anyone of the forums they have across the nation so you can see the location of the IP, displayed as your location when you make a post. Once you make a random post on Topix.net, you will see the IP location you are connected to and how it displays on Topix.net. You then decide whether or not you want to post under that location. All Topix.net forum posts show the location of the IP associated with each individual post.
Should you prefer to have your post show a different IP than what it is currently showing, you simply log off the Blackberry software, then log back on to get a new IP and repeat the same steps until you get the location you desire.
That is how they were able to initially manipulate their “location” while posting on Topix.net and elsewhere to make it appear there was a hoard of posters when it was only these two nut cases.
The two of them attempted to engage me in some sick sex talk on Facebook chat during that time. It was in that immediate moment that I “knew” who they were. She was the one who started the sex talk and I immediately retreated from the chat and blocked them. I “knew” who they were and what their game was and it was a perverted and sick game they were playing.
They were hunting.
HE KILLED LISA STEBIC. And he is the “covert operative” that Lisa Stebic knew as “John Morgan”—John Jr.—who is symbolically represented as “Joe Pistone”. This is one of the “two” “front teeth” who are Tony’s children who are his cover.
This guy was “daremeonce” on Greasy.com and “slickster” on Blogster.com and “islanddude58” elsewhere.
His female partner was “islandgirl” on Blogster.com.
This guy is “Joe Swift”. These two have created a plethora of online identities. More recently, in the past year or so, they were involved in MMA fighting and had posted all over the internet regarding that sport and were involved in the online forums dedicated to MMA fighting.
They are VERY active on the internet and it is because of this activity that I have not only been able to track them; but because of their prolific internet activity, I have been able to see them psychically as clear as a cloudless day.
Since that time in the summer of 2009, I have tracked down many of their bogus online identities. As with many of the other bogus identities I’ve tracked down, they use real people’s photos yet manipulate them by using the old photos taken when those individuals were younger creating a separate identity based on those old photos yet use more recent photos of the same people as completely different identities. While some of the created identities are extensive and intricately created, I can still clearly see them for who they are with my instinctive “sense of knowing.” I then use what I know to track down the fictitious identities they have created as proof of what I already “knew.” These two are so sloppy; however, and I‘ve been able to track them all across the internet to loads of different identities.
I have copies of these plagiarized photos and false identities on file. He is an internet predator.
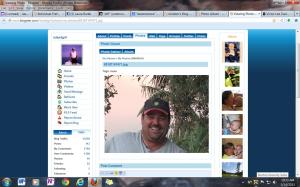 He uses the name “Vic”, “Victor Lee”, “Lee Davis”, Vic Davis” and a combination of that name. She goes by the name of “Marty”. They play the ruse that they both work for “BP” and travel across the nation working at BP sites. Notice the “BP” hat in the picture.
He uses the name “Vic”, “Victor Lee”, “Lee Davis”, Vic Davis” and a combination of that name. She goes by the name of “Marty”. They play the ruse that they both work for “BP” and travel across the nation working at BP sites. Notice the “BP” hat in the picture.
I can’t post this page because it contains details that cannot be revealed just yet; however, I want to point out that on 06.20.10 they provided me with the BP logo and told me that he is the guy who is “Tony S” and associated with the location of the quarry pay loaders traveling along the long bumpy road. And this guy is not only directly associated with “John Spira” and Lisa Stebic; but this guy is also associated with “Stacy Peterson”. On this particular page in the session is one of the many times spirit provided me with the location of Stacy Peterson.
 On 01.24.11 page 4, they show me a cell phone, a different one than the other two they showed me. They tell me here that on this phone, in time, the “father” (Tony) will use this as a “play phone”. That means he will create some shenanigans utilizing my phone or the digital information of my phone. Spirit tells me that this guy “Jabber Jaws” will be in the news and this will be a “face-off” between him and his female partner. The session ends showing his pointing-the-finger-at-me-hand as his pointing finger is poking through the lower loop of the cursive “L” on “Lisa”.
On 01.24.11 page 4, they show me a cell phone, a different one than the other two they showed me. They tell me here that on this phone, in time, the “father” (Tony) will use this as a “play phone”. That means he will create some shenanigans utilizing my phone or the digital information of my phone. Spirit tells me that this guy “Jabber Jaws” will be in the news and this will be a “face-off” between him and his female partner. The session ends showing his pointing-the-finger-at-me-hand as his pointing finger is poking through the lower loop of the cursive “L” on “Lisa”.
 As it turns out, the cell phone shown to me, on 01.24.11 p4, is a cell phone I first started using in the late spring/early summer of 2011. I remember when I saw this phone in the session, it was more detailed than I cared to draw, and I didn’t document the color or any specifics. This is one of those times when I was too tired or too lazy to draw the details, thinking it wasn’t that important. However, now, while composing this little e-book here, I’ve realized how important it is to draw things exactly as they are shown to me and/or document all the little details for future reference because those details are very important.
As it turns out, the cell phone shown to me, on 01.24.11 p4, is a cell phone I first started using in the late spring/early summer of 2011. I remember when I saw this phone in the session, it was more detailed than I cared to draw, and I didn’t document the color or any specifics. This is one of those times when I was too tired or too lazy to draw the details, thinking it wasn’t that important. However, now, while composing this little e-book here, I’ve realized how important it is to draw things exactly as they are shown to me and/or document all the little details for future reference because those details are very important.
The information on the specific cell phones that were shown to me throughout the years as I have detailed in this Chapter 4—cell phones I later acquired and used—showing that my phone calls, texts, and internet access was being tapped, tracked and recorded, clearly show the gross level of manipulation and illegal activity this guy is engaging in to maintain his façade.
Because I knew the illegal tapping activities he was engaging in on me and why he was doing what he was doing, I relayed false information over the phone regarding the work I was doing and who was who based on the symbolism’s provided to me through spirit communication. I’ve sent BS emails to associates to send him in the wrong direction knowing he would plagiarize my work in an effort to set me up and then point the finger at me. I’ve stated numerous bogus things regarding my sessions over the phone while talking to my associate.
Early last year in 2013, I sent a bogus text messages to my associate about where to look for a “humerus bone”—in Lockport where the old arched limestone bridge used to be—because I “knew” he would steal that and use it some way. This along with the many bogus text messages I’ve sent to myself the past six months and the bogus information I’ve posted on my blogs over the years knowing he is using that information to twist the investigations will be what brings these two down.
I’ve left a trail of tainted breadcrumbs for these two baboons to gobble up and use in their twisted schemes—all in an effort to trap the idiots and prove that they are illegally tapping all of my communications for their own benefit and gain while simultaneously trying to frame me in the process. I have been feeding them with garbage for YEARS. And they have taken that bait to the moon.
Now, there is no way for them to get out of this.
BRAINTREE Ch. 5 – Planting Digital Evidence
Copyright Notice
The material in this site is copyright protected.
Copyright Notice
All material on this site https://whereabouts67.wordpress.com not covered by other copyright and not explicitly marked as public domain is copyright ©2009-2014 Laura L. Burke
Material can be linked to only.
A link to exit directly to the main page: Missing – Lisa Stebic – Stacy Peterson – John Spira – Home Page
Tags: Des Plaines River, illinois, John Spira, Lisa Stebic, Rockdale, Stacy Peterson


August 24, 2018 at 7:06 PM |
The Cell Phone: Illegal Wiretaps | MISSING
[…]A consumer is at liberty to curtail the time spent for his or her psychic readings.[…]